OpenPGP is an open standard (RFC 4880) that uses cryptographic algorithms, including public-key algorithms, symmetric cipher algorithms, etc., to encrypt data. It is used for digitally signing, encrypting, or decrypting text, files, emails, etc. TurboPGP is a command-line PGP software tool created based on OpenPGP to protect confidential file data and ensure data integrity and authenticity.
Cryptographic Operations of TurboPGP
- Generate an OpenPGP key pair.
- Import a user's public or secret key.
- Encrypt or decrypt a file using the OpenPGP standard.
- Digitally sign a file and verify OpenPGP signatures.
To download the 30-day free trial of TurboPGP, you can go to its homepage. The PGP encryption software can natively run on Windows, Linux, and macOS. The command line syntax and options are the same for all the supported platforms. We now demonstrate its use on Windows.
Once installed, run the following command in Powershell to confirm the installation was successful:
tbpgp
Example:
tbpgp
[2022/08/12 07:01:27 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
no operation option switch present.Generating a PGP Key Pair
Before you can commence encrypting and decrypting files, documents, or any data of your choice, you need to generate a key pair for encryption and decryption.
These keys are essential when you want to encrypt your data and when the recipient wants to decrypt the message received. TurboPGP comes in handy to create this key pair as it provides a key generator to create an OpenPGP key pair. Type the following command to generate an OpenPGP key pair:
tbpgp --gen-key "{username} <{user_email}>"
Example:
tbpgp --gen-key "john smith <john smith@test.com>"
[2022/08/10 07:15:08 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/10 07:15:08 +0000] load_keychain: 5 keys loaded from secret key chain
[2022/08/10 07:15:08 +0000] load_keychain: 5 keys loaded from public key chain
Enter passphrase of secret key: ****
[2022/08/10 07:15:17 +0000] key id B303E88F84D203A2 added to secret keychain
[2022/08/10 07:15:17 +0000] key id B303E88F84D203A2 added to public keychainTwo keys have been generated, i.e., one public and one secret key, with each key being stored in their public keyring and secret keyring, respectively. Note: Your email should be enclosed within the < >; otherwise, you'll get an invalid name address pair error.
To view the generated keys, type the following command:
# list all the public keys
tbpgp --list-keys
# list all the secret keys
tbpgp --list-secret-keysExample:
tbpgp --list-keys
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/12 07:08:59 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/12 07:08:59 +0000] load_keychain: 1 keys loaded from public key chain
public keyring: C:\Users\alvin\AppData\Roaming\TurboSoft\TurboPGP\pubring.tpg
pub RSA 2048 84D203A2 2022-08-10
uid john smith <john.smith@test.com>
sub RSA 2048 6267DA83 2022-08-10
tbpgp --list-secret-keys
[2022/08/12 07:18:24 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/12 07:18:25 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/12 07:18:25 +0000] load_keychain: 1 keys loaded from public key chain
secret keyring: C:\Users\alvin\AppData\Roaming\TurboSoft\TurboPGP\secring.tpg
sec RSA 2048 84D203A2 2022-08-10
uid john smith <john.smith@test.com>
ssb RSA 2048 6267DA83 2022-08-10The good thing is that you can export your public key to a user you want to communicate with. The user will use this public key to encrypt their messages. To export, type the command:
tbpgp --export "key ID" --output <filename>
Replace "key ID" with your generated public key, e.g., "D733FDCC". Replace
Example:
tbpgp --export "D733FDCC" --output "my_publicKey.txt"
[2022/08/12 07:32:20 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/12 07:32:20 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/12 07:32:20 +0000] load_keychain: 1 keys loaded from public key chain
[2022/08/12 07:32:20 +0000] public key 'D733FDCC' exported to 'my_publicKey.txt'Signing Files
A PGP signature is a unique sequence of octets generated against a given block of digital data. Generating a PGP signature involves hashing the entire block of payload data, be it a file or a particular PGP certificate, mixed with predefined data like timestamps. The hash value is then encrypted with a given public-key cryptographic algorithm like RSA to derive the signature.
TurboPGP can generate two types of signed files with an attached or detached signature.
- Signed file: The file's content is signed, with the signature attached. Usually denoted with a .pgp extension.
- Detached signature file: It's the signature stored in an individual file, leaving the original file and its contents intact.
A detached signature file is denoted with a .sig extension.
Run the following commands on your terminal with a specified public key:
tbpgp --sign <filename> --signer <keyID>
Example:
tbpgp --sign k.txt --signer "D733FDCC"
[2022/08/11 06:42:06 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/11 06:42:06 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/11 06:42:06 +0000] load_keychain: 1 keys loaded from public key chain
[2022/08/11 06:42:06 +0000] key lookup: found secret-key keyid D733FDCC
Enter passphrase of secret key: *
[2022/08/11 06:42:15 +0000] successfully created signed file 'k.txt.pgp' from john smith <john.smith@test.com>The above command creates a signed file denoted with .pgp extension.
Note: Specifying outputFile is optional; it will automatically generate one with a .pgp extension.
tbpgp --sign <filename> --signer <keyID> -o <filename.sig> --detached
The above one creates a detached signature file denoted with .sig extension.
Example:
tbpgp --sign "k.txt" --signer "D733FDCC" -o "k.txt.sig" --detached
[2022/08/10 18:36:29 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/10 18:36:29 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/10 18:36:29 +0000] load_keychain: 1 keys loaded from public key chain
[2022/08/10 18:36:29 +0000] key lookup: found secret-key keyid D733FDCC
Enter passphrase of secret key: *
[2022/08/10 18:36:44 +0000] successfully created detached signature 'k.txt.sig' from john smith <john.smith@test.com>.Signature Verification
Why do we need to verify a signature? A signature is verified basically to confirm the file at hand is from who the owner claims to be. Signature verification authenticates a file, text, or any data from the original owner.
TurboPGP verifies a digital signature in two ways depending on signature attachment with the below command syntax:
# verify a signed file (signature attached)
tbpgp --verify <signedFile>
# verify a detached signature
tbpgp --verify <detachedSignature> <originalFile>Example:
tbpgp -verify k.txt.pgp
[2022/08/11 07:08:49 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/11 07:08:50 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/11 07:08:50 +0000] load_keychain: 1 keys loaded from public key chain
[2022/08/11 07:08:50 +0300] OpenPGP signed file with attached signature: 'k.txt.pgp'
[2022/08/11 07:08:50 +0000] key lookup: found secret-key keyid DC2CBE11D733FDCC
Enter passphrase of secret key: *
[2022/08/11 07:08:56 +0300] Verification was successful for signature 'k.txt.pgp' from john smith <john.smith@test.com>.Example:
tbpgp -v k.txt.sig k.txt
[2022/08/11 07:11:17 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/11 07:11:18 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/11 07:11:18 +0000] load_keychain: 1 keys loaded from public key chain
[2022/08/11 07:11:18 +0300] OpenPGP detached signature file: 'k.txt.sig'
[2022/08/11 07:11:18 +0300] OpenPGP signed file: 'k.txt'
[2022/08/11 07:11:18 +0000] key lookup: found secret-key keyid DC2CBE11D733FDCC
Enter passphrase of secret key: *
[2022/08/11 07:12:11 +0300] Verification was successful for signature 'k.txt.sig' from john smith <john.smith@test.com>.The importance of digital signatures is that they can be employed to prove the file is indeed from the owner of this public key and has not been tampered with.
Encryption
Encryption conceals a message by converting plain text into an unreadable format known as ciphertext. To encrypt with TurboPGP, use the following syntax:
tbpgp --encrypt <inputFile> --recipient <keyID> -o <outputFile>
or
tbpgp -e <inputFile> -r <keyID> -o <outputFile>
Example:
tbpgp --encrypt "b.txt" --recipient "D733FDCC"
[2022/08/12 08:19:45 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/12 08:19:45 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/12 08:19:45 +0000] load_keychain: 1 keys loaded from public key chain
[2022/08/12 08:19:45 +0000] key lookup: found secret-key keyid D733FDCC
Enter passphrase of secret key: *
[2022/08/12 08:19:47 +0000] successfully encrypted 'b.txt' to 'b.txt.pgp' (primary keyID=DC2CBE11D733FDCC, uid='john smith <john.smith@test.com>')Example 2: When supplied file path or filename has spaces, enclose the argument in double quotes. e.g., "Hello world"
tbpgp -e "Hello world.txt" -r "D733FDCC"
[2022/08/12 09:39:26 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/12 09:39:26 +0000] load_keychain: 6 keys loaded from secret key chain
[2022/08/12 09:39:26 +0000] load_keychain: 6 keys loaded from public key chain
[2022/08/12 09:39:26 +0000] key lookup: found secret-key keyid D733FDCC
Enter passphrase of secret key: *
[2022/08/12 09:39:29 +0000] successfully encrypted 'Hello world.txt' to 'Hello world.txt.pgp' (primary keyID=DC2CBE11D733FDCC, uid='john smith <john.smith@test.com>')If we open an encrypted file with Notepad in Windows, we see the contents are unreadable. 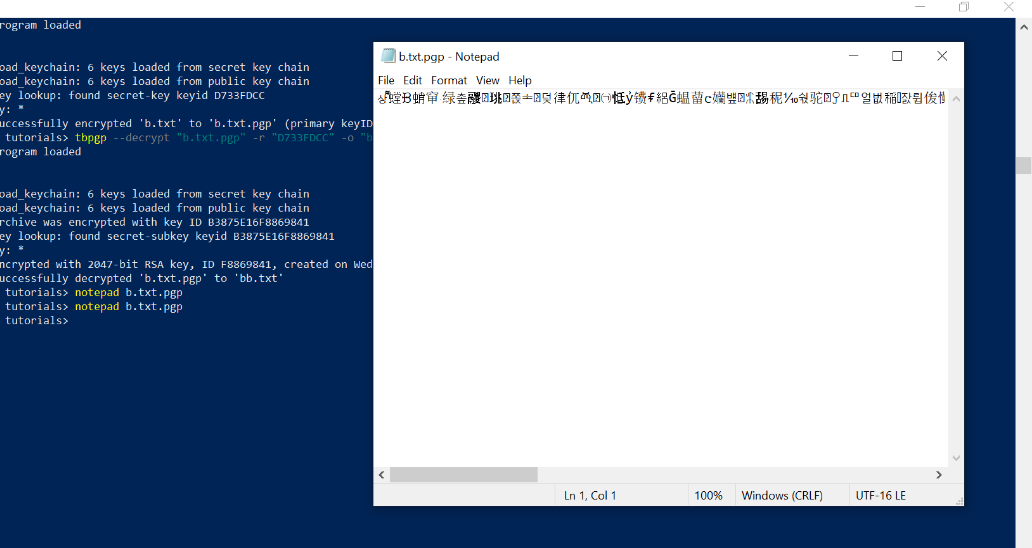
NOTE: By default, TurboPGP names the encrypted file by appending a ".pgp" extension.
Decryption
Decryption is the reverse process of encryption. It converts encrypted data into its original form. TurboPGP can decrypt a PGP encrypted file with the following command syntax:
tbpgp --decrypt <inputFile> -r <keyID> -o <outputFile>
For instance:
tbpgp --decrypt "b.txt.pgp" -r "D733FDCC" -o "bb.txt"
[2022/08/12 08:22:49 +0300] program loaded
Evaluation days left: 30
Expired: 0 DEFAULT.
[2022/08/12 08:22:49 +0000] load_keychain: 1 keys loaded from secret key chain
[2022/08/12 08:22:49 +0000] load_keychain: 1 keys loaded from public key chain
[2022/08/12 08:22:49 +0000] archive was encrypted with key ID B3875E16F8869841
[2022/08/12 08:22:49 +0000] key lookup: found secret-subkey keyid B3875E16F8869841
Enter passphrase of secret key: *
[2022/08/12 08:22:51 +0000] encrypted with 2041-bit RSA key, ID F8869841, created on Wed Aug 10 06:57:24 2022, user "john smith <john.smith@test.com>"
[2022/08/12 08:22:51 +0000] successfully decrypted 'b.txt.pgp' to 'bb.txt'The output above shows that the encrypted file was successfully decrypted to the output file bb.txt. The file can now be viewed and read as shown below with Notepad.
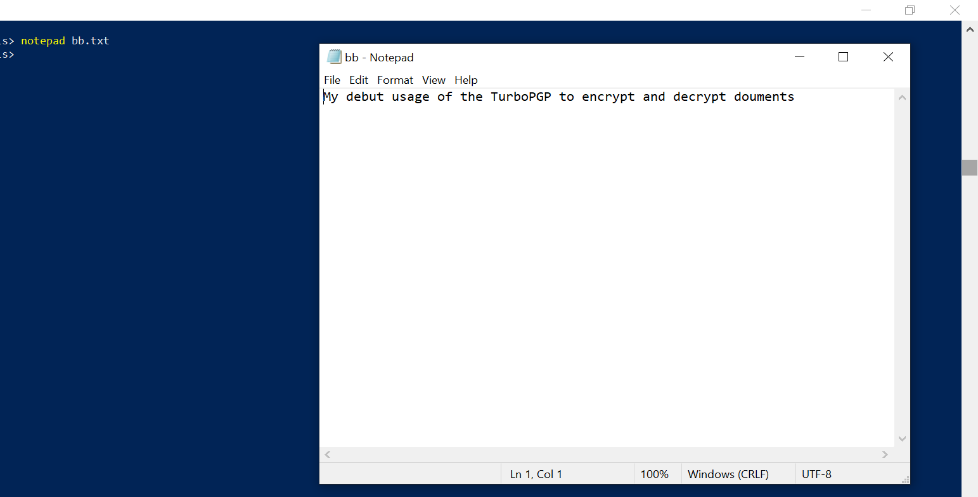
Above, we have demonstrated the primary usage of PGP software TurboPGP Command Line on Windows.

